leads4pass updated the latest EC-COUNCIL 312-50v11 dumps with VCE and PDF. All problems have been corrected,
100% guaranteed true and effective, to help you pass the exam smoothly. Visit https://www.leads4pass.com/312-50v11.html (429 Q&As) and select 312-50v11 dumps PDF or 312-50v11 dumps VCE to ensure the success of the exam
[EC-COUNCIL 312-50v11 exam pdf] EC-COUNCIL 312-50v11 exam PDF uploaded from google drive, online download provided by the latest update of leads4pass:
https://drive.google.com/file/d/1ap2P_piJ8AP8BkaxrqHnXqc1XjVbrYaN/
Latest update EC-COUNCIL 312-50v11 exam questions and answers online practice test
QUESTION 1
What is the main security service a cryptographic hash provides?
A. Integrity and ease of computation
B. Message authentication and collision resistance
C. Integrity and collision resistance
D. Integrity and computational in-feasibility
Correct Answer: D
QUESTION 2
What is the minimum number of network connections in a multi-homed firewall?
A. 3
B. 5
C. 4
D. 2
Correct Answer: A
QUESTION 3
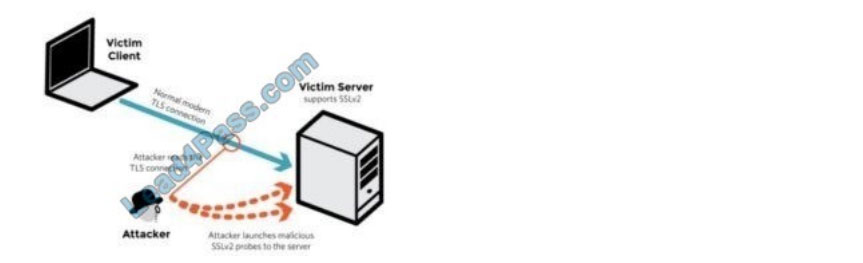
Samuel a security administrator, is assessing the configuration of a web server. He noticed that the server permits
SSlv2 connections and the same private key certificate is used on a different server that allows SSLv2 connections.
This vulnerability makes the web server vulnerable to attacks as the SSLv2 server can leak key information.
Which of the following attacks can be performed by exploiting the above vulnerability?
A. DROWN attack
B. Padding oracle attack
C. Side-channel attack
D. DUHK attack
Correct Answer: A
DROWN is a serious vulnerability that affects HTTPS and other services that deem SSL and TLS, some of the essential
cryptographic protocols for network security. These protocols allow everyone on the net to browse the net, use email, look online, and send instant messages while not third parties being able to browse the communication. DROWN allows
attackers to break the encryption and read or steal sensitive communications, as well as passwords, credit card
numbers, trade secrets, or financial data. At the time of public disclosure in March 2016, our measurements indicated
thirty a third of all HTTPS servers were vulnerable to the attack. fortuitously, the vulnerability is much less prevalent
currently. As of 2019, SSL Labs estimates that one.2% of HTTPS servers are vulnerable. What will the attackers
gain? Any communication between users and the server. This typically includes, however isn\\’t limited to, usernames
and passwords, credit card numbers, emails, instant messages, and sensitive documents. under some common
scenarios, an attacker can also impersonate a secure website and intercept or change the content the user sees. Who
is vulnerable? Websites, mail servers, and other TLS-dependent services are in danger for the DROWN attack. At the
time of public disclosure, many popular sites were affected. we used Internet-wide scanning to live how many sites are
vulnerable:
SSLv2 Operators of vulnerable servers got to take action. there \\’s nothing practical that browsers or end-users will do
on their own to protect against this attack. Is my site vulnerable? Modern servers and shoppers use the TLS encryption
protocol. However, because of misconfigurations, several servers also still support SSLv2, the 1990s- era precursor to
TLS. This support did not matter in practice, since no up-to-date clients really use SSLv2. Therefore, despite the fact
that SSLv2 is thought to be badly insecure, until now, simply supporting SSLv2 wasn\\’t thought of as a security problem, is
clients never used it. DROWN shows that merely supporting SSLv2 may be a threat to fashionable servers and
clients. It modern associate degree attacker to modern fashionable TLS connections between up-to-date clients and
servers by sending probes to a server that supports SSLv2 and uses the same private key.
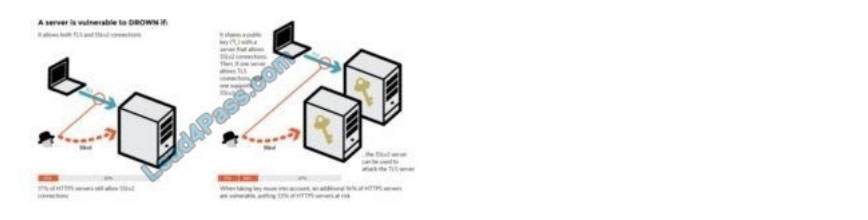
SSLv2 It allows SSLv2 connections. This is surprisingly common, due to misconfiguration and inappropriate default
settings. Its private key is used on any other server that allows SSLv2 connections, even for another protocol. Many
companies reuse the same certificate and key on their web and email servers, for instance. In this case, if the email
server supports SSLv2 and the web server does not, an attacker can take advantage of the email server to break TLS
connections to the webserver. A server is vulnerable to DROWN if:
SSLv2 How do I protect my server? To protect against DROWN, server operators need to ensure that their private keys
software used anyplace with server computer code that enables SSLv2 connections. This includes net servers, SMTP
servers, IMAP and POP servers, and the other software that supports SSL/TLS. Disabling SSLv2 is difficult and
depends on the particular server software. we offer instructions here for many common products: OpenSSL: OpenSSL
may be a science library employed in several server merchandises. For users of OpenSSL, the simplest and
recommended solution is to upgrade to a recent OpenSSL version. OpenSSL
1.0.2 users ought to upgrade to 1.0.2g. OpenSSL 1.0.1 users ought to upgrade to one.0.1s. Users of older OpenSSL
versions ought to upgrade to either one in every one of these versions. (Updated March thirteenth,
16:00 UTC) Microsoft IIS (Windows Server): Support for SSLv2 on the server aspect is enabled by default only on the
OS versions that correspond to IIS 7.0 and IIS seven.5, particularly Windows scene, Windows Server 2008, Windows
seven, and Windows Server 2008R2. This support is disabled within the appropriate SSLv2 subkey for `Server\\’, as
outlined in KB245030. albeit users haven\\’t taken the steps to disable SSLv2, the export-grade and 56-bit ciphers that
build DROWN possible don\\’t seem to be supported by default. Network Security Services (NSS): NSS may be a
common science library designed into several server merchandises. NSS versions three.13 (released back in 2012) and
higher than ought to have SSLv2 disabled by default. (A little variety of users might have enabled SSLv2 manually and
can get to take steps to disable it.) Users of older versions ought to upgrade to a more modern version. we tend to still
advocate checking whether or not your non-public secret is exposed elsewhere Other affected software and in operation
systems: Instructions and data for Apache, Postfix, Nginx, Debian, Red Hat Browsers, and other consumers: practical
nothing practical that net browsers or different client computer code will do to stop DROWN. only server operators are
ready to take action to guard against the attack.
QUESTION 4
While examining audit logs, you discover that people are able to telnet into the SMTP server on port 25. You would like
to block this, though you do not see any evidence of an attack or other wrongdoing. However, you are concerned about
affecting the normal functionality of the email server. From the following options choose how best you can achieve this
objective?
A. Block port 25 at the firewall.
B. Shut off the SMTP service on the server.
C. force all connections to use a username and password.
D. Switch from Windows Exchange to UNIX Sendmail.
E. None of the above.
Correct Answer: E
QUESTION 5
What piece of hardware on a computer\\’s motherboard generates encryption keys and only releases a part of the key
so that decrypting a disk on a new piece of hardware is not possible?
A. CPU
B. GPU
C. UEFI
D. TPM
Correct Answer: D
QUESTION 6
What would be the fastest way to perform content enumeration on a given web server by using the Gobuster tool?
A. Performing content enumeration using the brute force mode and 10 threads
B. Shipping SSL certificate verification
C. Performing content enumeration using a wordlist
D. Performing content enumeration using the brute force mode and random file extensions
Correct Answer: D
QUESTION 7
You have the SOA presented below in your Zone.
Your secondary servers have not been able to contact your primary server to synchronize information. How long will the
secondary servers attempt to contact the primary server before it considers that zone is dead and stops responding to
queries?
collegae.edu.SOA, cikkye.edu ipad.college.edu. (200302028 3600 3600 604800 3600)
A. One day
B. One hour
C. One week
D. One month
Correct Answer: C
QUESTION 8
Which of the following viruses tries to hide from anti-virus programs by actively altering and corrupting the chosen
service call interruptions when they are being run?
A. Macro virus
B. Stealth/Tunneling virus
C. Cavity virus
D. Polymorphic virus
Correct Answer: B
QUESTION 9
If a token and 4-digit personal identification number (PIN) is used to access a computer system and the token
performs off-line checking for the correct PIN, what type of attack is possible?
A. Birthday
B. Brute force
C. Man-in-the-middle
D. Smurf
Correct Answer: B
QUESTION 10
During the enumeration phase. Lawrence performs banner grabbing to obtain information such as OS details and
versions of services running. The service that he enumerated runs directly on TCP port 445. Which of the following
services is enumerated by Lawrence in this scenario?
A. Server Message Block (SMB)
B. Network File System (NFS)
C. Remote procedure call (RPC)
D. Telnet
Correct Answer: A
Explanation: Worker Message Block (SMB) is an organization document sharing and information texture convention.
SMB is utilized by billions of gadgets in a different arrangement of working frameworks, including Windows, macOS, iOS
, Linux, and Android. Customers use SMB to get information on workers. This permits sharing of records, unified
information the board, and brought down capacity limit needs for cell phones. Workers additionally use SMB as a
feature of the Software-characterized Data Center for outstanding burdens like grouping and replication. Since SMB is a
far-off record framework, it requires security from assaults where a Windows PC may be fooled into reaching a
pernicious worker running inside a confided-in organization or to a far-off worker outside the organization’s edge. Firewall
best practices and arrangements can upgrade security keeping malevolent traffic from leaving the PC or its
organization. For Windows customers and workers that don\\’t have SMB shares, you can obstruct all inbound SMB
traffic utilizing the Windows Defender Firewall to keep far-off associations from malignant or bargained gadgets. In the
Windows Defender Firewall incorporates the accompanying inbound principles.
You should also create a new blocking rule to override any other inbound firewall rules. Use the following suggested
settings for any Windows clients or servers that do not host SMB Shares: Name: Block all inbound SMB 445
Description: Blocks all inbound SMB TCP 445 traffic. Not to be applied to domain controllers or computers that host
SMB shares. Action: Block the connection Programs: All Remote Computers: Any Protocol Type: TCP Local Port: 445
Remote Port: Any Profiles: All Scope (Local IP Address): Any Scope (Remote IP Address): Any Edge Traversal: Block
edge traversal You must not globally block inbound SMB traffic to domain controllers or file servers. However, you can
restrict access to them from trusted IP ranges and devices to lower their attack surface. They should also be restricted
to Domain or Private firewall profiles and not allow Guest/Public traffic.
QUESTION 11
in an attempt to increase the security of your network, you Implement a solution that will help keep your
wireless network undiscoverable and accessible only to those that know It.
How do you accomplish this?
A. Delete the wireless network
B. Remove all passwords
C. Lock all users
D. Disable SSID broadcasting
Correct Answer: D
QUESTION 12
When you are getting information about a web server, it is very important to know the HTTP Methods (GET, POST,
HEAD, PUT, DELETE, TRACE) that are available because there are two critical methods (PUT and DELETE). PUT can
upload a file to the server and DELETE can delete a file from the server. You can detect all these methods (GET,
POST, HEAD, DELETE, PUT, TRACE) using NMAP script engine. What Nmap script will help you with this task?
A. HTTP-methods
B. HTTP enum
C. HTTP-headers
D. HTTP-git
Correct Answer: A
QUESTION 13
Suppose that you test an application for the SQL injection vulnerability. You know that the backend database
is based on Microsoft SQL Server. In the login/password form, you enter the following credentials:
Username: attack\\’ or 1?
Password: 123456
Based on the above credentials, which of the following SQL commands are you expecting to be executed by the server,
if there is indeed an SQL injection vulnerability?
A. select * from Users where UserName =\\’attack or 1=1 -and UserPassword = \\’123456″
B. select * from users wherefuserName = \\’attack\\’ or 1=1 –\\’and UserPassword = \\’123456\\’
C. select * from Users where UserName =\\’attack” or 1=1 -and UserPassword = \\’123456\\’
D. select * from users where UserName”\\’attack\\’or 1=1 – and UserPassword “\\’123456\\’
Correct Answer: D
Share part of the 312-50v11 exam pdf, 312-50v11 exam questions and answers, and 312-50v11 exam videos for free. Obtain the complete 312-50v11 exam dumps path.
For information about leads4pass 312-50v11 Dumps (including PDF and VCE), please visit: https://www.leads4pass.com/312-50v11.html (429 Q&As)
ps.
Get free EC-COUNCIL 312-50v11 dumps PDF online: https://drive.google.com/file/d/1ap2P_piJ8AP8BkaxrqHnXqc1XjVbrYaN/
![[2017 New Version] Free Latest Cisco 100-105 Dumps PDF Materials And VCE Youtube Demo](https://www.latestvce.com/wp-content/themes/blogstream/img/thumb-medium.png)
