
Get free EC-COUNCIL 312-38 exam practice questions online can help you improve your exam success rate.
Free EC-COUNCIL 312-38 exam questions are part of leads4pass 312-38 Exam Dumps. Get the complete 312-38 Exam Dumps https://www.leads4pass.com/312-38.html (Total Questions: 562 Q&A) helps you pass the exam 100% successfully. All exam questions and answers come from EC-COUNCIL exam experts. Guaranteed to be true and valid!
All examination questions are updated throughout the year to ensure immediate validity.
The latest update EC-COUNCIL 312-38 PDF download online
Free EC-COUNCIL 312-38 exam PDF download online. All exam PDFs are part of the latest update from leads4pass EC-COUNCIL 312-38 PDF. Get the complete EC-COUNCIL 312-38 PDF at leads4pass
The latest updated EC-COUNCIL 312-38 exam practice questions online free practice
QUESTION 1
Which of the following steps are required in an idle scan of a closed port? Each correct answer represents a part of the
solution. Choose all that apply.
A. The attacker sends a SYN/ACK to the zombie.
B. The zombie\\’s IP ID increases by only 1.
C. In response to the SYN, the target sends a RST.
D. The zombie ignores the unsolicited RST, and the IP ID remains unchanged.
E. The zombie\\’s IP ID increases by 2.
Correct Answer: ACDB
Following are the steps required in an idle scan of a closed port:
1.Probe the zombie\\’s IP ID: The attacker sends a SYN/ACK to the zombie. The zombie, unaware of the SYN/ACK,
sends back a RST, thus disclosing its IP ID. 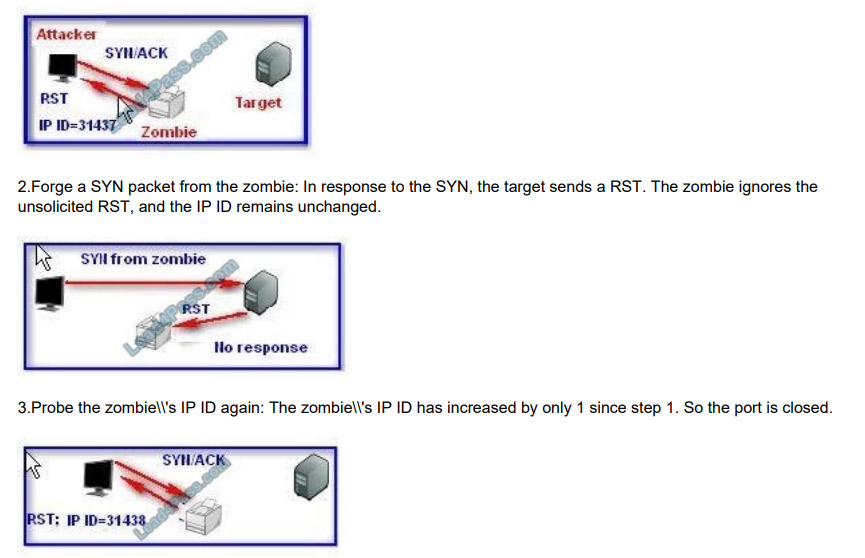
QUESTION 2
Which of the following modems offers wireless communication under water?
A. Controllerless modem
B. Short haul modem
C. Acoustic modem
D. Optical modem
Correct Answer: C
QUESTION 3
Which of the Windows security component is responsible for controlling access of a user to Windows resources?
A. Network Logon Service (Netlogon)
B. Security Accounts Manager (SAM)
C. Security Reference Monitor (SRM)
D. Local Security Authority Subsystem (LSASS)
Correct Answer: D
QUESTION 4
Which of the following honeypots is a useful little burglar alarm?
A. Backofficer friendly
B. Specter
C. Honeynet
D. Honeyd
Correct Answer: A
QUESTION 5
Which of the following firewalls are used to monitor the status of active connections, and configure the network packets
to pass through the firewall? Each correct answer represents a complete solution. Choose all that apply.
A. Farm owner
B. Proxy server
C. Dynamic packet filtering
D. The circuit gateway
Correct Answer: AC
QUESTION 6
Which of the following is a technique for gathering information about a remote network protected by a firewall?
A. Firewalking
B. Warchalking
C. Wardriving
D. Wardialing
Correct Answer: A
Fire walking is a technique for gathering information about a remote network protected by a firewall. This technique can
be used effectively to perform information gathering attacks. In this technique, an attacker sends a crafted packet with a
TTL value that is set to expire one hop past the firewall. If the firewall allows this crafted packet through, it forwards the
packet to the next hop. On the next hop, the packet expires and elicits an ICMP “TTL expired in transit” message to the
attacker. If the firewall does not allow the traffic, there should be no response, or an ICMP “administratively prohibited”
message should be returned to the attacker. A malicious attacker can use firewalking to determine the types of ports/
protocols that can bypass the firewall. To use firewalking, the attacker needs the IP address of the last known gateway
before the firewall and the IP address of a host located behind the firewall. The main drawback of this technique is that if
an administrator blocks ICMP packets from leaving the network, it is ineffective. Answer option B is incorrect.
Warchalking is the drawing of symbols in public places to advertise an open Wi-Fi wireless network. Having found a WiFi node, the warchalker draws a special symbol on a nearby object, such as a wall, the
pavement, or a lamp post. The name warchalking is derived from the cracker terms war dialing and war driving. Answer
option C is incorrect. War driving, also called access point mapping, is the act of locating and possibly exploiting
connections to wireless local area networks while driving around a city or elsewhere. To do war driving, one needs a
vehicle, a computer (which can be a laptop), a wireless Ethernet card set to work in promiscuous mode, and some kind
of an antenna which can be mounted on top of or positioned inside the car. Because a wireless LAN may have a range
that extends beyond an office building, an outside user may be able to intrude into the network, obtain a free Internet
connection, and possibly gain access to company records and other resources. Answer option D is incorrect. War
dialing or wardialing is a technique of using a modem to automatically scan a list of telephone numbers, usually dialing
every number in a local area code to search for computers, Bulletin board systems, and fax machines. Hackers use the
resulting lists for various purposes, hobbyists for exploration, and crackers – hackers that specialize in computer security
– for password guessing.
QUESTION 7
Assume that you are working as a network administrator in the head office of a bank. One day a bank employee
informed you that she is unable to log in to her system. At the same time, you get a call from another network
administrator informing you that there is a problem connecting to the main server. How will you prioritize these two
incidents?
A. Based on a first come first served basis
B. Based on the type of response needed for the incident
C. Based on a potential technical effect of the incident
D. Based on approval from management
Correct Answer: C
QUESTION 8
Henry, head of network security at Gentech, has discovered a general report template that someone has reserved only
for the CEO. Since the file has to be editable, viewable, and deletable by everyone, what permission value should he
set?
A. 700
B. 777
C. 755
D. 600
Correct Answer: B
QUESTION 9
You are advising a school district on disaster recovery plans. In case a disaster affects the main IT centers for the
district they will need to be able to work from an alternate location. However, budget is an issue. Which of the following
is most appropriate for this client?
A. Warm site
B. Cold site
C. Hot site
D. Off site
Correct Answer: B
A cold site provides an office space, and in some cases basic equipment. However, you will need to restore your data to
that equipment in order to use it. This is a much less expensive solution than the hot site. Answer option C is incorrect.
A
hot site has equipment installed, configured and ready to use. This may make disaster recovery much faster, but will
also be more expensive. And a school district can afford to be down for several hours before resuming IT operations, so
the
less expensive option is more appropriate.
Answer option A is incorrect. A warm site is between a hot and cold site. It has some equipment ready and connectivity
ready. However, it is still significantly more expensive than a cold site, and not necessary for this scenario.
Answer option D is incorrect. Off site is not any type of backup site terminology.
QUESTION 10
With which of the following forms of acknowledgment can the sender be informed by the data receiver about all
segments that have arrived successfully?
A. Block Acknowledgment
B. Negative Acknowledgment
C. Cumulative Acknowledgment
D. Selective Acknowledgment
Correct Answer: D
Selective Acknowledgment (SACK) is one of the forms of acknowledgment. With selective acknowledgments, the
sender can be informed by a data receiver about all segments that have arrived successfully, so the sender retransmits
only those segments that have actually been lost. The selective acknowledgment extension uses two TCP options: The
first is an enabling option, “SACK-permitted”, which may be sent in a SYN segment to indicate that the SACK option can
be used once the connection is established. The other is the SACK option itself, which can be sent over an established
connection once permission has been given by “SACK-permitted”. Answer option A is incorrect. Block Acknowledgment
(BA) was initially defined in IEEE 802.11e as an optional scheme to improve the MAC efficiency. IEEE 802.11n capable
devices are also referred to as High Throughput (HT) devices. Instead of transmitting an individual ACK for every
MPDU, multiple MPDUs can be acknowledged together using a single BA frame. Block Ack (BA) contains bitmap size of
64*16 bits. Each bit of this bitmap represents the status (success/ failure) of an MPDU. Answer option B is incorrect.
With Negative Acknowledgment, the receiver explicitly notifies the sender which packets, messages, or segments were
received incorrectly that may need to be retransmitted. Answer option C is incorrect. With Cumulative Acknowledgment,
the receiver acknowledges that it has correctly received a packet, message, or segment in a stream which implicitly
informs the sender that the previous packets were received correctly. TCP uses cumulative acknowledgment with its
TCP sliding window.
QUESTION 11
Which of the following policies helps in defining what users can and should do to use network and organization\\’s
computer equipment?
A. General policy
B. Remote access policy
C. IT policy
D. User policy
Correct Answer: D
A user policy helps in defining what users can and should do to use network and organization\\’s computer equipment. It
also defines what limitations are put on users for maintaining the network secure such as whether users can install
programs on their workstations, types of programs users are using, and how users can access data.
Answer option C is incorrect. IT policy includes general policies for the IT department. These policies are intended to
keep the network secure and stable. It includes the following:
Virus incident and security incident
Backup policy
Client update policies
Server configuration, patch update, and modification policies (security)
Firewall policies Dmz policy, email retention, and auto forwarded email policy
Answer option A is incorrect. It defines the high level program policy and business continuity plan.
Answer option B is incorrect. Remote access policy is a document that outlines and defines acceptable methods of
remotely connecting to the internal network.
QUESTION 12
The IP addresses reserved for experimental purposes belong to which of the following classes?
A. Class E
B. Class C
C. Class A
D. Class D
Correct Answer: A
QUESTION 13
Which of the following is the practice of sending unwanted e-mail messages, frequently with commercial content, in
large quantities to an indiscriminate set of recipients? Each correct answer represents a complete solution. Choose all
that apply.
A. Email spoofing
B. Junk mail
C. E-mail spam
D. Email jamming
Correct Answer: BC
E-mail spam, also known as unsolicited bulk email (UBE), junk mail, or unsolicited commercial email (UCE), is the
practice of sending unwanted e-mail messages, frequently with commercial content, in large quantities to an
indiscriminate set of recipients. Answer option A is incorrect. Email spoofing is a fraudulent email activity in which the
sender address and other parts of the email header are altered to appear as though the email originated from a different
source. Email spoofing is a technique commonly used in spam and phishing emails to hide the origin of the email
message. By changing certain properties of the email, such as the From, Return-Path and Reply-To fields (which can be
found in the message header), ill-intentioned users can make the email appear to be from someone other than the
actual sender. The result is that, although the email appears to come from the address indicated in the From field (found
in the email headers), it actually comes from another source. Answer option D is incorrect. Email jamming is the use of
sensitive words in e-mails to jam the authorities that listen in on them by providing a form of a red herring and an
intentional annoyance. In this attack, an attacker deliberately includes “sensitive” words and phrases in otherwise
innocuous emails to ensure that these are picked up by the monitoring systems. As a result, the senders of these emails
will eventually be added to a “harmless” list and their emails will be no longer intercepted, hence it will allow them to
regain some privacy.
leads4pass is updated throughout the year. EC-COUNCIL 312-38 exam dumps https://www.leads4pass.com/312-38.html (PDF + VCE).
Guaranteed immediate validity! All exam questions have been verified to ensure that they are true and valid!
ps.
Free EC-COUNCIL 312-38 exam PDF download online. All exam PDFs are part of the latest update from leads4pass EC-COUNCIL 312-38 PDF.
Get the complete EC-COUNCIL 312-38 PDF at leads4pass

