
leads4pass updated the latest EC-COUNCIL ECSAV10 dumps with VCE and PDF. All problems have been corrected,
100% guaranteed true and effective, to help you pass the exam smoothly. Visit https://www.leads4pass.com/ecsav10.html (354 Q&As) and select ECSAV10 dumps PDF or ECSAV10 dumps VCE to ensure the success of the exam
[EC-COUNCIL ECSAV10 exam pdf] EC-COUNCIL ECSAV10 exam PDF uploaded from google drive, online download provided by the latest update of leads4pass:
https://drive.google.com/file/d/1dizrL7OQWfKypZH1nAzfU2UJ6umhwR4Z/
Latest update EC-COUNCIL ECSAV10 exam questions and answers online practice test
QUESTION 1
Today, most organizations would agree that their most valuable IT assets reside within applications and databases.
Most would probably also agree that these are areas that have the weakest levels of security, thus making them the
prime target for malicious activity from system administrators, DBAs, contractors, consultants, partners, and customers. 
Which of the following flaws refers to an application using poorly written encryption code to securely encrypt and store
sensitive data in the database and allows an attacker to steal or modify weakly protected data such as credit card
numbers, SSNs, and other authentication credentials?
A. SSI injection attack
B. Insecure cryptographic storage attack
C. Hidden field manipulation attack
D. Man-in-the-Middle attack
Correct Answer: B
QUESTION 2
What does ICMP Type 3/Code 13 mean?
A. Host Unreachable
B. Port Unreachable
C. Protocol Unreachable
D. Administratively Blocked
Correct Answer: D
QUESTION 3
What is kept in the following directory? HKLM\SECURITY\Policy\Secrets
A. Service account passwords in plain text
B. Cached password hashes for the past 20 users
C. IAS account names and passwords
D. Local store PKI Kerberos certificates
Correct Answer: A
QUESTION 4
Amazon, an IT based company, conducts a survey on the usage of the Internet. They found that company employees
spend most of the time at work surfing the web for their personal use and for inappropriate web site viewing.
Management decide to block all such web sites using URL filtering software.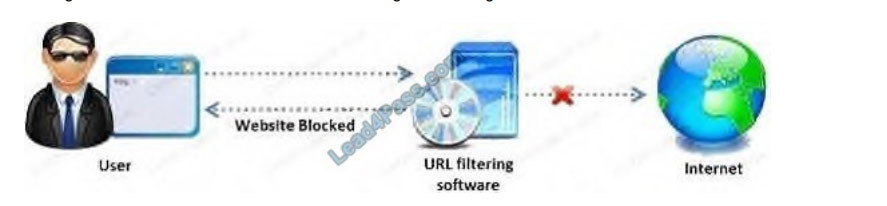
How can employees continue to see the blocked websites?
A. Using session hijacking
B. Using proxy servers
C. Using authentication
D. Using encryption
Correct Answer: B
QUESTION 5
Which of the following is NOT related to the Internal Security Assessment penetration testing strategy?
A. Testing to provide a more complete view of site security
B. Testing focused on the servers, infrastructure, and the underlying software, including the target
C. Testing including tiers and DMZs within the environment, the corporate network, or partner company connections
D. Testing performed from a number of network access points representing each logical and physical segment
Correct Answer: B
QUESTION 6
Peter works as a lead penetration tester in a security service firm named Xsecurity. Recently, Peter was assigned a
white-box pen test assignment testing the security of an IDS system deployed by a client. During the preliminary
information gathering, Peter discovered the TTL to reach the IDS system from his end is 30. Peter created a Trojan and
fragmented it in to 1-character packets using the Colasoft packet builder tool. He then used a packet flooding utility to
bombard the IDS with these fragmented packets with the destination address of a target host behind the IDS whose TTL
is 35. What is Peter trying to achieve?
A. Peter is trying to bypass the IDS system using a Trojan
B. Peter is trying to bypass the IDS system using the broadcast address
C. Peter is trying to bypass the IDS system using the insertion attack
D. Peter is trying to bypass the IDS system using inconsistent packets
Correct Answer: D
QUESTION 7
Paulette works for an IT security consulting company that is currently performing an audit for the firm ACE Unlimited.
Paulette\\’s duties include logging on to all the company\\’s network equipment to ensure IOS versions are up-to-date
and all the other security settings are as stringent as possible. Paulette presents the following screenshot to her boss so
he can inform the clients about necessary changes need to be made. From the screenshot, what changes should the
client company make? Exhibit:
A. The banner should not state “only authorized IT personnel may proceed”
B. Remove any identifying numbers, names, or version information
C. The banner should include the Cisco tech support contact information as well
D. The banner should have more detail on the version numbers for the network equipment
Correct Answer: B
QUESTION 8
War Driving is the act of moving around a specific area, mapping the population of wireless access points
for statistical purposes. These statistics are then used to raise awareness of the security problems
associated with these types of networks.
Which one of the following is a Linux based program that exploits the weak IV (Initialization Vector)
problem documented with static WEP?
A. Airsnort
B. Aircrack
C. WEPCrack
D. Airpwn
Correct Answer: A
QUESTION 9
Adam is a senior penetration tester at XYZsecurity Inc. He is auditing a wireless network for vulnerabilities.
Before starting the audit, he wants to ensure that the wireless card in his machine supports injection. He
decided to use the latest version of aircrack-ng tool.
Which of the following commands will help Adam check his wireless card for injection?
A. aireplay-ng -9 wlan0
B. airodump-ng wlan0
C. airdecap-ng -3 wlan0
D. aireplay-ng -5 –b wlan0
Correct Answer: B
QUESTION 10
You are the security analyst working for a private company out of France. Your current assignment is to obtain credit
card information from a Swiss bank owned by that company. After initial reconnaissance, you discover that the bank
security defenses are very strong and would take too long to penetrate. You decide to get the information by monitoring
the traffic between the bank and one of its subsidiaries in London. After monitoring some of the traffic, you see a lot of
FTP packets traveling back and forth. You want to sniff the traffic and extract usernames and passwords. What tool
could you use to get this information?
A. RaidSniff
B. Snort
C. Ettercap
D. Airsnort
Correct Answer: C
QUESTION 11
What are the scanning techniques that are used to bypass firewall rules and logging mechanisms and disguise
themselves as usual network traffic?
A. Connect Scanning Techniques
B. SYN Scanning Techniques
C. Stealth Scanning Techniques
D. Port Scanning Techniques
Correct Answer: C
QUESTION 12
Vulnerability assessment is an examination of the ability of a system or application, including the current security
procedures and controls, to withstand assault.
What does a vulnerability assessment identify?
A. Disgruntled employees
B. Weaknesses that could be exploited
C. Physical security breaches
D. Organizational structure
Correct Answer: B
QUESTION 13
TCP/IP provides a broad range of communication protocols for the various applications on the network. The TCP/IP
model has four layers with major protocols included within each layer. Which one of the following protocols is used to
collect information from all the network devices?
A. Simple Network Management Protocol (SNMP)
B. Network File system (NFS)
C. Internet Control Message Protocol (ICMP)
D. Transmission Control Protocol (TCP)
Correct Answer: A
Share part of the ECSAV10 exam pdf, ECSAV10 exam questions and answers, and ECSAV10 exam videos for free. Obtain the complete ECSAV10 exam dumps path.
For information about leads4pass ECSAV10 Dumps (including PDF and VCE), please visit: https://www.leads4pass.com/ecsav10.html (354 Q&As)
ps. Get free EC-COUNCIL ECSAV10 dumps PDF online: https://drive.google.com/file/d/1dizrL7OQWfKypZH1nAzfU2UJ6umhwR4Z/

